Getting Started With Nitro
Initial Requirements
This topic provides information for browser requirements and instructions for signing into Nitro.
Browser Requirements
Use any of the following to access the Nitro Admin Console:
- Chrome
- Firefox
- Microsoft Edge
- Internet Explorer 11
Requesting a User Account
To request a new user account, submit a support ticket.
Signing into Nitro
Depending on the location of your Nitro cluster, the sign in URL varies.
- For customers in North America - https://cdw-02-app-us.veevanitro.com/login
- For customers in Europe - https://cdw-app-eu.veevanitro.com/login
- For customers in Asia-pacific - https://cdw-app-ap.veevanitro.com/login
The Nitro Admin Console (NAC) supports single sign-on (SSO), allowing users to sign into Nitro with their corporate logins. To support SSO, Nitro uses an external identity provider to authenticate users and pass user information in web browser requests. The customer’s IdP, for example, Okta, must be accessible from the internet, either directly or through a broker or gateway.
To configure SSO for Nitro:
- Sign into the NAC as an admin user.
- Select Identity Providers from the Users menu.
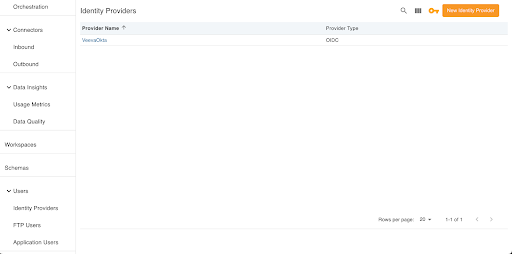
- Select New Identity Provider. Nitro supports OIDC and SAML provider types.
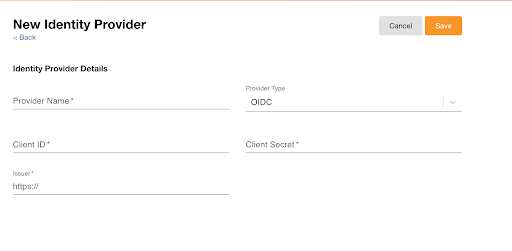
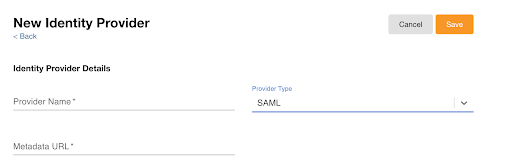
- Enter the appropriate information.
- Select Save.
- Configure the corporate identity provider to include the NAC as an application for one of the following provider types:
OIDC SAML Sign-in Redirect URIs
https://<cluster name>.auth.<region>.amazoncognito.com/oauth2/idpresponse
Where <cluster name> is the exact cluster name, except where there is an underscore. Underscores must be changed to hyphen.
Where <region> is one of the following:
- Us-east-2
- Eu-central-1
- ap-northeast-1
Single Sign-on URL
https://<cluster name>.auth.<region>.amazoncognito.com/saml2/idpresponse
Where <cluster name> is the exact cluster name, except where there is an underscore. Underscores must be changed to hyphen.
Where <region> is one of the following:
- Us-east-2
- Eu-central-1
- ap-northeast-1
Initiate login URI
US: https://cdw-02-app-us.veevanitro.com/oauth2/authorization/<cluster name>
EU: https://cdw-app-eu.veevanitro.com/oauth2/authorization/<cluster name>
AP: https://cdw-app-ap.veevanitro.com/oauth2/authorization/<cluster name>
Where <cluster name> is exactly as it is in the NAC. Case sensitive. Do not convert any underscores to a hyphen.
Audience Restriction
urn:amazon:cognito:sp:<cognito pool id>
Select the key icon on the Identity Provider page to view.
To sign into the NAC using SSO:
-
Navigate to the NAC sign in page.
-
Enter your corporate email address. This is not your NAC username.
-
Select Continue.
-
Select the appropriate cluster and username if a user’s corporate email is associated with multiple NAC users, then select Continue.
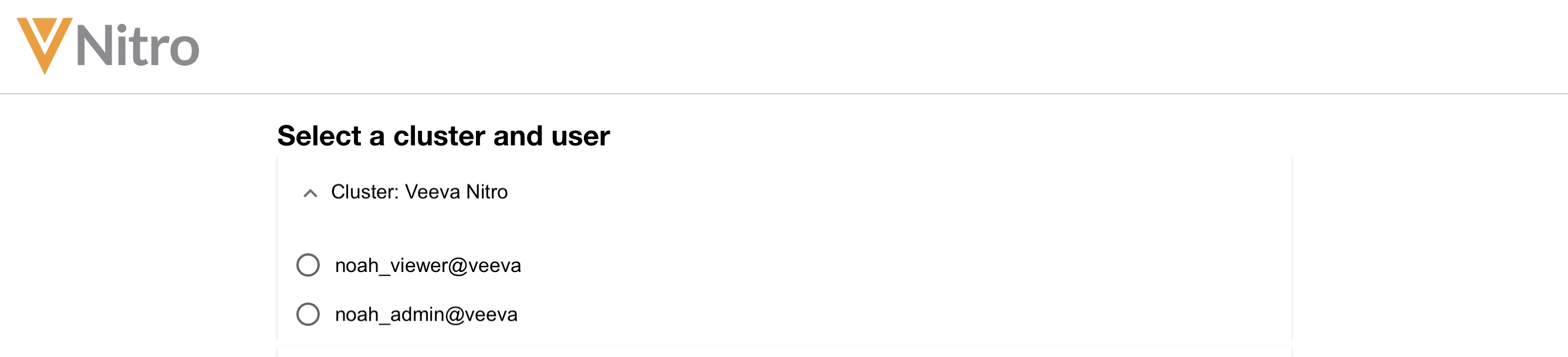
-
Enter your corporate IdP password.
-
Select Continue. The NAC job history page displays.
To sign into the NAC using an NAC username and password:
-
Navigate to the NAC login page.
-
Enter your NAC username.
-
Select Continue.
-
Enter your NAC password.
-
Select Continue. The NAC job history page displays.
Syncing Revoked IDP Users with NAC Users
Admins can sync deactivated users in a corporate IDP with their NAC users. This allows admins to easily sync user IDs with Nitro when a user is removed from their corporate IDP.
To sync deactivated Nitro users:
- Generate a Nitro API key.
- Submit the following request payload to the Nitro API from the corporate IDP with an email address parameter to deactivate the mapped Nitro application user.
For example:
curl --location --request PUT ‘URL/api/v1/admin/users/deactivate' \
--header 'Authorization: [API key]’ \
--header 'Content-Type: application/json' --data-raw '{"email" : “john.smith@veeva.com”}’Request Payload
{
"john.smith@veeva.com"
}
Response will return a user that was deactivated with a status code
Example Response
{
"responseStatus": "SUCCESS,
"data": [
{
"userName" : "john@veevaProd",
"tenant" : "veevaProd",
"status" : "inactive",
"RedshiftUser: "vcdw_john_smith"
}
]
}
IP Addresses for SFTP
Nitro uses static IP addresses for its SFTP Server, where customers and data vendors deposit various text files to load data. See Static IP Addresses for more information.
Signing into External Tools
See External Tools for more information on connecting to Nitro via external tools.
In order for a connection to be established between Nitro and the BI tool, configure the necessary network security items on the Nitro side and if required, on the BI tool side:
- The public-facing IP address of the BI tool application must be allowlisted in Nitro configuration. This is done by submitting a support ticket with the IP(s) representing the network from which the BI tool is connecting.
- If a corporate firewall is in place, outbound/inbound traffic to the Nitro database IP and port may need to be allowlisted/opened. If this is needed, submit a support ticket to get the right connection info needed for the Nitro database.


